Step 1
If you have a home desktop PC, mac or personal notebook, you may access for free or can download a management software such as Microsoft Money to help design your own free excel budget template.
Step2
Design your excel budget template around 6 main categories.
Step 3
Debts should include any credit loans and monthly balance you choose to pay make up the next budget category on your free excel template.
Step 4
Miscellaneous expenses
Step 5
Figure total monthly income at top of your free excel budget template, then total your monthly expenses for each category, and subtract to get your net income balance at the bottom.
Monday, December 29, 2008
Thursday, December 25, 2008
Season Greetings
Wednesday, December 24, 2008
Nintendo DSi

The latest Revision of the Nintendo DS, the DSi (with its main new feature being 2 built-in cameras, with a more multimedia focus of pics/music), is now available in Japan.
But all of us North Americans want to know, when can we get our hands on it? Looks like the DSi will land in North America sometime this upcoming summer.
Monday, December 22, 2008
Next Podcast
January 3 2009
ACDSEE Photo Manager 2009
Winzip 12
Logitech Quickcam Deluxe For Notebooks
ACDSEE Photo Manager 2009
Winzip 12
Logitech Quickcam Deluxe For Notebooks
Friday, December 19, 2008
Wednesday, December 17, 2008
Monday, December 15, 2008
Choosing The Right Laptop
Step 1
Decide what you want to do on your
laptop.
Step 2
Decide what screen size you need.
Step3
Decide what kind of networking features you want. One of the most popular current features of laptops is wireless Internet access.
Step4
Determine your battery needs.
Step5
Look into the warranty and service plan.
Decide what you want to do on your
laptop.
Step 2
Decide what screen size you need.
Step3
Decide what kind of networking features you want. One of the most popular current features of laptops is wireless Internet access.
Step4
Determine your battery needs.
Step5
Look into the warranty and service plan.
Friday, December 12, 2008
Apple 16GB iPod nano
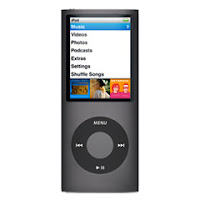
The 16GB iPod nano has curvaceous aluminum and glass design, you can watch movies and shows in widescreen, automatically create Genius playlists and flip through album art with Cover Flow. Plus, with a simple shake, it’s even easier to shuffle your way to a different song.
Check it out
Wednesday, December 10, 2008
Open ID
What is OpenID?
OpenID has arisen from the open source community to solve the problems that could not be easily solved by other existing technologies. OpenID is a lightweight method of identifying individuals that uses the same technology framework that is used to identify websites. As such, OpenID is not owned by anyone, nor should it be
OpenID eliminates the need for multiple usernames across different websites, simplifying your online experience.
You get to choose the OpenID Provider that best meets your needs and most importantly that you trust. your OpenID can stay with you, no matter which Provider you move to and is completely free.
With OpenID you can easily transform one of these existing URIs into an account which can be used at sites which support OpenID logins.
Today it is estimated that there are nearly ten-thousand sites supporting OpenID logins. More Info
Get your Open ID now
OpenID has arisen from the open source community to solve the problems that could not be easily solved by other existing technologies. OpenID is a lightweight method of identifying individuals that uses the same technology framework that is used to identify websites. As such, OpenID is not owned by anyone, nor should it be
OpenID eliminates the need for multiple usernames across different websites, simplifying your online experience.
You get to choose the OpenID Provider that best meets your needs and most importantly that you trust. your OpenID can stay with you, no matter which Provider you move to and is completely free.
With OpenID you can easily transform one of these existing URIs into an account which can be used at sites which support OpenID logins.
Today it is estimated that there are nearly ten-thousand sites supporting OpenID logins. More Info
Get your Open ID now
Anti Virus & Spyware
Monday, December 8, 2008
Friday, December 5, 2008
Wednesday, December 3, 2008
Monday, December 1, 2008
Blog: Top Ten Tips
1) Stay on topic
2) Be informative
3) Old news is not news
4) Adhere to a schedule
5) Clarity and simplicity
6) Keyword-rich
7) Quantity matters
8) Frequency
9) Spell checking and proof-reading
10) RSS
2) Be informative
3) Old news is not news
4) Adhere to a schedule
5) Clarity and simplicity
6) Keyword-rich
7) Quantity matters
8) Frequency
9) Spell checking and proof-reading
10) RSS
Friday, November 28, 2008
Sony VAIO 18.4" Laptop

Sony VAIO laptop and enjoy realistic, high definition Blu-ray movies on the huge 18.4" LCD in Full HD 1080p. Powered by an Intel Core 2 Duo processor and 4GB of RAM, you can go wireless, store data to the 320GB hard drive, play games with high-end graphics, connect via HDMI, and more with this digital powerhouse.
Check it out
Wednesday, November 26, 2008
Gmail exploit!!
Gmail exploit may allow attackers to forward e-mail
When you create a filter in your Gmail account, a request is sent to Google's servers to be processed. The request is made in the form of a url with many variables. For security reasons, your browser doesn't display all the variable contained within the url. Using FireFox and a plugin called Live HTTP Headers, you can see exactly what variables are sent from your browser to Google's servers.
After that, an attacker just needs to identify the variable that is the equivalent of the username.
To avoid being a victim of the vulnerability, users should check their filters often, Brandon suggests. Firefox users can download an extension called NoScript that helps prevent these attacks
When you create a filter in your Gmail account, a request is sent to Google's servers to be processed. The request is made in the form of a url with many variables. For security reasons, your browser doesn't display all the variable contained within the url. Using FireFox and a plugin called Live HTTP Headers, you can see exactly what variables are sent from your browser to Google's servers.
After that, an attacker just needs to identify the variable that is the equivalent of the username.
To avoid being a victim of the vulnerability, users should check their filters often, Brandon suggests. Firefox users can download an extension called NoScript that helps prevent these attacks
Monday, November 24, 2008
Friday, November 21, 2008
Wednesday, November 19, 2008
Monday, November 17, 2008
How To : Set up a wireless network
1 Plug the power in your router and give it approximately 10 sec to initialize. Then unplug the network cable or Ethernet cable from the back of your PC and connect it to the back of the router that is labeled "INTERNET"
2 Once your internet cable is plugged in you should have 4 available ports.
3 Once everything is connected you need to configure your router by opening a web browser and typing in http://192.168.1.1 in the address bar. Then hit enter.
4 The address will open up a sign on page. Generally the default user name and password is admin, admin. Once you get into the setup menu, under "basic setup" CHANGE THE ROUTER NAME. Then click on the Wireless tab, under "basic setup" and CHANGE YOUR WIRELESS NETWORK NAME. Scroll down at the bottom and save your settings.
5 To configure your security settings click the Wireless tab and click "wireless security." You will have a drop down menu for WEP Encryption this can be as long as you want to be. Choose a pass phrase and click Generate. A list of WEP keys will be generated for you and this is the key you would use to connect to wirelessly.
6 Finally Click on Administration tab at the top of the page and change your default password for accessing your wireless router setup pages, by typing a new router password and then confirming that password. Make sure you click save to at the bottom of the menu for your changes to take affect.
7 Check your wireless connection with a laptop that has a wireless card either built into it or connected to it. On your lab top right click the little monitor at the bottom right hand corner of your task bar and then click "view wireless networks". If you dont see any networks click "refresh network list" on the top left hand corner of your wireless network config box. This should show you the wireless networks around you and you can click on it to disable or enable your connection via the password you set up.
2 Once your internet cable is plugged in you should have 4 available ports.
3 Once everything is connected you need to configure your router by opening a web browser and typing in http://192.168.1.1 in the address bar. Then hit enter.
4 The address will open up a sign on page. Generally the default user name and password is admin, admin. Once you get into the setup menu, under "basic setup" CHANGE THE ROUTER NAME. Then click on the Wireless tab, under "basic setup" and CHANGE YOUR WIRELESS NETWORK NAME. Scroll down at the bottom and save your settings.
5 To configure your security settings click the Wireless tab and click "wireless security." You will have a drop down menu for WEP Encryption this can be as long as you want to be. Choose a pass phrase and click Generate. A list of WEP keys will be generated for you and this is the key you would use to connect to wirelessly.
6 Finally Click on Administration tab at the top of the page and change your default password for accessing your wireless router setup pages, by typing a new router password and then confirming that password. Make sure you click save to at the bottom of the menu for your changes to take affect.
7 Check your wireless connection with a laptop that has a wireless card either built into it or connected to it. On your lab top right click the little monitor at the bottom right hand corner of your task bar and then click "view wireless networks". If you dont see any networks click "refresh network list" on the top left hand corner of your wireless network config box. This should show you the wireless networks around you and you can click on it to disable or enable your connection via the password you set up.
Friday, November 14, 2008
Logitech QuickCam

QuickCam Communicate STX takes your video communications to the next level. Clear video with VGA quality and RightLight Technology provides improved image clarity even in dim lighting.
Check It Out
Wednesday, November 12, 2008
AVG update cripples some Windows XP systems
On Tuesday A update for AVG 8 suggested that a Windows system file is a Trojan horse, and users who delete the file form the system could leave their Windows XP systems endlessly rebooting or unable to reboot at all. The problem only affects users of AVG 8 products running the Dutch, French, Italian, Portuguese, and Spanish language versions of Windows XP. AVG immediately sent out a corrected update to its customers, including those using the free editions of AVG.
Monday, November 10, 2008
Friday, November 7, 2008
Wednesday, November 5, 2008
Monday, November 3, 2008
SMS Gmail Delayed
Going play around with the new send-to-SMS chat feature in Gmail you'll have to wait a little longer.
The glitch, is about two weeks to fix, would keep the two-way communication feature from turning on all the way, keeping replies from making it back to you.
The glitch, is about two weeks to fix, would keep the two-way communication feature from turning on all the way, keeping replies from making it back to you.
Friday, October 31, 2008
Wednesday, October 29, 2008
Installing SQL Server
Step 1: Prepare Your Computer to Install SQL Server 2005
To prepare your computer for SQL Server 2005, review hardware and software requirements, System Configuration Checker requirements and blocking issues, and security considerations.
Step 2: Install SQL Server
To install SQL Server, run Setup using the SQL Server 2005 Installation Wizard or install from the command prompt. You can also add components to an instance of SQL Server 2005, or upgrade to SQL Server 2005 from a previous SQL Server version.
Step 3: Configure Your SQL Server Installation
After Setup completes the installation of SQL Server , you can configure SQL Server using graphical and command prompt utilities.
More Information
To prepare your computer for SQL Server 2005, review hardware and software requirements, System Configuration Checker requirements and blocking issues, and security considerations.
Step 2: Install SQL Server
To install SQL Server, run Setup using the SQL Server 2005 Installation Wizard or install from the command prompt. You can also add components to an instance of SQL Server 2005, or upgrade to SQL Server 2005 from a previous SQL Server version.
Step 3: Configure Your SQL Server Installation
After Setup completes the installation of SQL Server , you can configure SQL Server using graphical and command prompt utilities.
More Information
Monday, October 27, 2008
Friday, October 24, 2008
Wednesday, October 22, 2008
Monday, October 20, 2008
Friday, October 17, 2008
Samsung 1080p 50" Flat-Panel Plasma HDTV
Wednesday, October 15, 2008
Windows XP Activation Problem
A problem is preventing Windows from accurately
checking the license for this computer!
There is an error code at the end.
Microsoft has an article about this
particular error and here is the link.
checking the license for this computer!
There is an error code at the end.
Microsoft has an article about this
particular error and here is the link.
Tuesday, October 14, 2008
Monday, October 13, 2008
Friday, October 10, 2008
Wednesday, October 8, 2008
Monday, October 6, 2008
Friday, October 3, 2008
Gateway DX4200-UB001A

64-bit Windows Vista aids memory efficiency; largest hard drive at this price,
and its specs and overall performance is great, well worth it!
Check It Out
Wednesday, October 1, 2008
Cisco Releases Router Security Patches
Cisco has issued a set of security patches for the Internet Operating System (IOS) software, used to power its routers and switches.
One of the bugs, a flaw in the Simple Network Management Protocol (SNMP) could be exploited by an attacker to seize control of the router. However, only specially configured Cisco uBR10012 series devices are affected.
One of the bugs, a flaw in the Simple Network Management Protocol (SNMP) could be exploited by an attacker to seize control of the router. However, only specially configured Cisco uBR10012 series devices are affected.
Monday, September 29, 2008
Friday, September 26, 2008
Wednesday, September 24, 2008
Friday, September 19, 2008
Fujitsu ScanSnap Scanner for the Mac

The Fujitsu ScanSnap S300M is the world’s smallest duplex ADF scanner, optimized for the Apple Macintosh system. It comes loaded with big features that make document management on the go as easy.
Check It Out
Wednesday, September 17, 2008
Apple releases Mac OS X 10.5.5
Apple has released the latest version of Leopard,
with bug fixes and security updates accompanying
the fifth update to the operating system.
with bug fixes and security updates accompanying
the fifth update to the operating system.
Monday, September 15, 2008
Friday, September 12, 2008
Thursday, September 11, 2008
Wednesday, September 10, 2008
Monday, September 8, 2008
Now Available: Internet Explorer 8 Beta 2
Internet Explorer 8 Beta 2 is now available. Internet Explorer 8 features a brand new Compatibility View, enhancements to help users get their everyday activities on the Web done faster. And all the features IT Pros expect!
Get it now
Get it now
Friday, September 5, 2008
Nintendo DS Lite

Nintendo DS Lite is a high-powered handheld video game system in a sleek folding design - loaded with features for a unique gaming experience.
Check it out
Wednesday, September 3, 2008
Google Phone

Google has been in talks with Verizon Wireless about the possible implementation of the Google phone. No one knows what the “Google Phone” means, as theories run from an actual phone developed by Google to a phone running Google based software supporting their Adwords product. This article says its all about putting their applications on Verizon phones
Monday, September 1, 2008
Friday, August 29, 2008
Wednesday, August 27, 2008
Friday, August 22, 2008
i river X20 Media Player

Easy Wheel, Easy Control, Easy Adaptable Plays music, video, photos and more
Plays up to 22 hours/Video : Plays up to 6 hours
Supports music file such as MP3,WMA and OGG Q10
Built-in SD-Card Slot
FM radio and FM recording reservation
Chech it Out
Wednesday, August 20, 2008
Computer Security
There are three good, free, anti-virus programs I recommend:
AVG
Avast
Anti-vir
Also NOD32 from eset. It is very lightweight and highly effective. I do not recommend McAfee or Norton . They're just too bloated.
I recommend for fighting spyware:
Microsoft Defender (Vista, XP and W2K only)
Spybot Search & Destroy
AdAware
The best commercial programs are Spysweeper and Pest Patrol but I don't find they're particularly better
The best ways to fight spyware is not to get it in the first place. That means using Firefox for day-to-day surfing, avoiding music sharing programs, and being very careful when you visit web sites. Avoid allowing them to install software.
AVG
Avast
Anti-vir
Also NOD32 from eset. It is very lightweight and highly effective. I do not recommend McAfee or Norton . They're just too bloated.
I recommend for fighting spyware:
Microsoft Defender (Vista, XP and W2K only)
Spybot Search & Destroy
AdAware
The best commercial programs are Spysweeper and Pest Patrol but I don't find they're particularly better
The best ways to fight spyware is not to get it in the first place. That means using Firefox for day-to-day surfing, avoiding music sharing programs, and being very careful when you visit web sites. Avoid allowing them to install software.
Tuesday, August 19, 2008
Tweaking Vista
Click properties and make sure indexing is OFF.. it will take a few moments to complete this task so be patient and make sure you don't have any other apps running in the background or it will take forever to finish.
Another way you can get it thinking faster is if you go to your control panel, double click performance information and click Adjust Visual Effects in the Tasks column. Give Windows permission to access the settings, click on Adjust for best performance and click apply. At the expense of a pretty GUI (Graphical User Interface) its will significantly boost the speed of Vista.
There is also a neat little option called "ReadyBoost." If you have a Memory stick with 2GBs or more you can use the space on your memory stick to boost up your PC. Vista automatically asks you if you would like to use your mem stick for Readyboost as soon as you plug it in. There are plenty other ways you can boost the speed of your PC,
Another way you can get it thinking faster is if you go to your control panel, double click performance information and click Adjust Visual Effects in the Tasks column. Give Windows permission to access the settings, click on Adjust for best performance and click apply. At the expense of a pretty GUI (Graphical User Interface) its will significantly boost the speed of Vista.
There is also a neat little option called "ReadyBoost." If you have a Memory stick with 2GBs or more you can use the space on your memory stick to boost up your PC. Vista automatically asks you if you would like to use your mem stick for Readyboost as soon as you plug it in. There are plenty other ways you can boost the speed of your PC,
VIsta Problems
Vista is a great operating system, as a tech the 2 biggest problems that are encountered with Vista are;
1. Don't buy a Vista system with 512 megs of RAM (simply not enough to run it. it's like driving a bus with a 4 cilinder engine).
2. Do not install drivers or high level access programs (like an anti virus program) that are NOT Vista compatible. This damages the operating system and can lead to data loss ( it's like putting diesel in a normal gas car).
1. Don't buy a Vista system with 512 megs of RAM (simply not enough to run it. it's like driving a bus with a 4 cilinder engine).
2. Do not install drivers or high level access programs (like an anti virus program) that are NOT Vista compatible. This damages the operating system and can lead to data loss ( it's like putting diesel in a normal gas car).
Monday, August 18, 2008
Friday, August 15, 2008
Wednesday, August 13, 2008
Friday, August 8, 2008
MacBook Air
The design is revolutionary, but Apple's MacBook Air will appeal to a smaller, more specialized audience than the standard MacBook!
www.apple.com
www.apple.com
Thursday, August 7, 2008
Wednesday, August 6, 2008
Subscribe to:
Comments (Atom)











